East SIG Report – November 2022
23rd February 2023
Neil Muller
After welcoming members to the November meeting of East SIG, host Frank Maher outlined the night’s agenda below:
Presentation 1: Q&A with Georg Skarbek
Presentation 2: Reducing Vulnerability to Scams by John Swale
Presentation 3: Man-in-the-Middle Scams by Dave Botherway
Main presentation: Consumer Printer Evolution by Dave Botherway
Q&A by George Skarbek.
Question: As an occasional user of Microsoft Yammer, I used to access Yammer from an App on my Android phone. With MelbPC now using Google Spaces, how can I get an App on my phone similar to the one I had for Yammer?
Answer: [Phillip Lynch from iHelp] Google “Spaces” is already available on your Android phone. At the bottom of your Gmail screen is an icon for Google “Chat”. Click on the “Chat” icon and it will lead you to the “Spaces” area.
[Bill Ford] I use Gmail on my iPhone and at the bottom of the Gmail screen I have a “Spaces” icon. I also get notifications for Spaces the same as I do for emails.
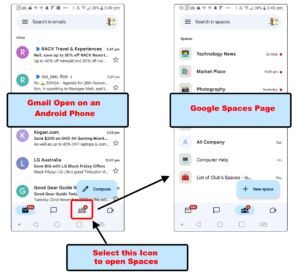
Figure 1 – Opening Google Spaces from Gmail on an Android Phone
As there were no further questions, George gave a brief summary of the Windows “Phone Link” app. This app enables users of Android Smart phones to access their phone from Windows, without touching the phone.
The “Phone Link” app wirelessly connects to and mirrors your Android phone on a Windows computer. The app enables users to read and send messages, view photos taken on your phone, view and run Android apps (only available on newer Android phones), view notifications and monitor phone calls.
When George is working on his computer, if a text message is received on his phone, a notification appears on the bottom of the computer screen. George found using the “Phone Link” app to make or reply to these messages, was far easier using a computer keyboard than on his phone. The app also makes it more convenient to access messages, notifications and calls, than to reach and type on a phone’s small screen.
George then displayed the home page of his Samsung Android phone on his computer screen. He then ran apps from his phone on his computer and demonstrated 3 apps he often uses. These were “Do not disturb”, “AtomicClock” and “Bubble”.
Reducing Vulnerability to Scams by John Swale
John commenced this presentation by asking the audience to consider the following questions when signing up to an organisation or website.
-
What data do organisations keep about you?
-
What data do they really need to keep?
-
How long do they keep this data online?
-
How long do they really need to keep it at all?
John highlighted a recent case where client and landlord data held online was scammed from the Melbourne City franchise of Estate agents Harcourts. When you view the data Harcourts kept on current and past individuals below, you have to ask whether they really needed to hold all that data?
Tenant data that was stolen included: full legal name, email address, address, phone number, copy of signature and photo identification.
Landlords’ and trades’ data stolen included: full legal name, email address, address, phone number, copy of signature and bank details.
In certain cases, the data you give out must be accurate, due to legal requirements such as for the government, health or for banking. However, in other cases, you may consider using approximate data. An example of this would be your date of birth. Many websites John uses, such as Woolworths, Coles, Bunnings etc., don’t need an accurate date of birth to identify you. Therefore, to reduce his vulnerability to scams, John varies the date of birth given. In his password manager John stores the date of birth he gives these firms. He varies this date for each site so if one site is hacked the date of birth is of no use for scammers to use to get into other sites.
What precautions should you take?
- Use complex passwords that are not easily guessed. Scammers will often look at your social networks for names that many people use as passwords, such as your dog, cat or children’s names.
- Use a Password manager and complex passwords. Most Password managers allow you to store the data you supplied a website.
- Use two factor authentication where possible.
- Where available many banks offer tokens that generate random numbers. For one-time passwords use your phone number. A finger print reader can also be used to identify who you are.
Audience comments
A member who recently completed a “Working with Children” certification, was concerned that the data he provided would be stored online. Once such a check has been approved, he felt his data should be moved offline.
Another member who also had to complete a police check for a “Working with Children” certification, was asked to supply a credit card number. He originally supplied an expired card, but was then asked for a current credit card number. This member queried why a current credit card was even needed, and he was concerned his data would be kept online.
Another member outlined that he monitors accounts he signs up to, by creating totally different email addresses for each account. He claims this method is not as complicated as you may think, as the accounts are aliases of just one account. Recently an account he set up for Bunnings using this technique, started getting scam emails. As Bunnings were the only company using that email address, it was obvious where the source of the hack came from. When he notified Bunnings that their email addresses had been scammed, unsurprisingly he did not hear back.
PayPal has recently been cited for maximising their dealings with its users for convenience over security, by sending out password checks by SMS when validating changes to passwords. It is well known that SMSs are not secure, however PayPal continues to use this technique on their site.
Man-in-the-Middle scams by Dave Botherway
An example of the Man-in-the-Middle scams was recently exposed on the “A Current Affair” television program, where the purchaser of a luxury car was scammed to the tune of $100,000. This type of scam is known as “business email compromise” and is the number one scam in Australia.
In the case highlighted in the TV show, the scammer hacked the car dealer’s email systems and impersonated the dealership. Emails from the purchaser of the vehicle, that he thought were directed to the car dealer, were actually redirected to a “man in the middle”. The purchasers’ emails were then sent from the scammers onto the car dealer. The car dealer then sent their return emails through the same redirection back to the purchaser. When payment was due, the scammers changed the bank details in the emails from the dealership to the customer, to the bank account set up by the scammers. When the purchaser transferred the money for the vehicle, the money was deposited in the scammers account. The scammers then emailed the car dealer to advise that payment was delayed, hence the scam was not detected for some time after the money was taken.
To avoid this type of scam, a quick phone call from the purchasers to the car dealership to check the account number would have discovered the scam.
The real estate sector is particularly attractive for this type of scam, because of the large lump sum money transfers involved. The buyer and estate agent don’t have a history of previous interaction, so this makes it harder to pick these types of scams.
The TV report relating to the scamming of the car buying can be viewed on YouTube at https://www.youtube.com/watch?v=Wk_nS9plbkQ
Consumer Printer Evolution by Dave Botherway
Dave Botherway gave our main presentation titled “Consumer Printer Evolution”. As the title suggests, Dave’s presentation takes us from the earliest consumer printer technology to the present day. The catalyst for Dave’s presentation were questions to him at the retirement village where he now lives, which showed a lack of understanding by many residents of what printers can do besides printing.
Dave commenced with a summary of how consumer printers have evolved over the years.
Early Line Printers
IBM Selectric
The IBM Selectric was an electric typewriter that featured a golf-ball-shaped type head that replaced the conventional typewriter’s type bars. The golf-ball-shaped design eliminated the jamming of the type bars and increased the typists’ speed and hence productivity. As a typist typed on the keyboard, the golf ball moved across the paper and rotated left and right to select the right character. Paper had to be fed in manually page by page as per a conventional typewriter of that era.

Figure 2 – IBM Selectric and various interchangeable typeheads
The golf ball head was interchangeable, enabling different fonts such as italics, scientific notation and other languages to be used. In 1964, a magnetic tape system for storing characters was added and the Selectric could be considered as the first word-processor.
Due to their speed (14.8 characters per second), immunity to clashing typebars, trouble-free paper path, high quality printed output, and reliability, Selectric-based mechanisms were also widely used as terminals for computers, replacing both Teletypes and older typebar-based output devices. One popular example was the IBM 2741 terminal. Among other applications, the 2741 (with a special typing element) figured prominently in the early years of the APL programming language. (WikiPedia)
A modified version of the Selectric saw use with IBM mainframe computers. Dave remembers using the Selectric for imputing data into a mainframe via a computer terminal.
IBM Matrix Line Printers
Matrix Line Printers were the first printers used by personal computers. They were connected to the computer by a 25-pin Centronics cable, which later became the standard for connecting printers to computers. Paper used was continuous sprocket-fed paper with the perforated edges able to be removed manually when printing was completed.
The print head moved across the paper and had a 5 x 7 or greater matrix. As the characters were selected the pins were fired onto a ribbon to put the image onto the paper. This was a breakthrough for early day computers.

Figure 3 – Matrix Line Printers

Figure 4 – An Early PC setup with a Matrix Printer
Inkjet Printers
Matrix printers were replaced by inkjet printers, with liquid ink being supplied by ink cartridges. Cartridges for colour inkjet printers came in 2 different types. The first type had a single cartridge for the 3 colours (Cyan, Magenta & Yellow) and a cartridge for Black), while the second type had separate cartridges for each colour and for black. A disadvantage with multi colour cartridges is when one of the colours runs out of ink, the whole cartridge has to be replaced.
Inkjet printers were cheap to buy, but cartridges were often more expensive than the printers. Manufacturers such as Canon, HP, Epson etc. hoped to recoup the cost of the printer over their life by selling genuine cartridges.

Figure 5 – Early Inkjet printer with a Black and a Multi colour cartridge
Because manufacturers’ genuine cartridges were expensive, kits could be purchased for users to refill their cartridges to reuse the cartridges again. As refilling cartridges was often messy, many chose to buy cheaper non-genuine cartridges online or at booths at shopping centres.
When refilling cartridges became more common, manufacturers incorporated an “empty lock” on their cartridges to prevent their reuse. However, users soon found techniques from others on the internet of how to override the “empty lock” and reset it so cartridges could be reused again.

Figure 6 – Individual colour cartridges with an ink refill kit.
To produce prints, inkjet printers have a print head that moves across the paper. The print head has multiple jets that ‘spray’ ink onto the paper.
Unlike early line printers that used sprocket-fed paper, inkjet printers used cheaper standard paper. Most used A4 paper, but a smaller number of commercial printers could use larger A3 paper.
A drawback with inkjet printers is when the printer is not used regularly, the inks can dry up and clog the print head.
Inkjet printers are able to print on different paper types, such as matt and glossy paper. They are also good for photo printing, although prints from places like Harvey Norman, Kmart, Officeworks etc often work out cheaper. When printing in colour, some printer models will wait for the ink to dry before printing the next sheet.
Laser Printers
Laser printers use a laser to draw an image onto an electrostatic drum to produce prints. The drum picks up “ink powder” and transfers the image onto the paper. A heating process then fuses the “ink powder” onto the paper.
Laser printers are usually larger than inkjet printers due to the electrostatic drum inside. Due to the heating process, they cannot use heat sensitive papers. They print one page at a time and are good for volume printing.
Laser printer are good if you regularly print a lot of documents and don’t need to print high resolution-coloured images.

Figure 7 – HP Black & White and Colour Laser printers
Printer functions
Multi-function printers or MFPs have become popular with home users because they can Print, Scan, Fax and Copy documents using a single device.

Figure 8 – Multi Function Printers
Read Function
MFP printers can read an image and then print it out as if it was a photocopier. They can also read an image and send it as a fax, although this is rarely used these days.
Copy Function
Many MFPs have a Copy function, that enables you to resize an image before printing it. This is either to increase or decrease the size of an image. Dave has found this feature useful when receiving printed instructions, usually from China, that are too small to easily read. Using the Copy function, he would increase the size of the image to make it more readable.
For archival purposes, images can be reduced in size with this function. Alternatively, the printer which would normally be set to print at 300dpi (dots per inch), can be set to a lower value such as 150dpi or less.
Double sided printing is a feature build into most printers that many people don’t realise they have, or consider too complicated to use.
Additional controls and functions from PC apps
When buying a new printer, software applications are often provided with a printer. However, many similar apps are available in Windows e.g. “Windows Fax & Scan” or as free or paid for 3rd party applications.
Printer connections
Cables
Printers are generally connected by a cable to the computer. Originally this was by a 25 pin “Parallel” cable, but this type of connection has now been replaced by the faster USB cables.
To make a print using a cable connection requires the computer to be turned on.
Wi-Fi
Laptop and phones connect to the internet by Wi-Fi from a modem router, but Wi-Fi can also give these devices access to the printer.
For printers connected by a cable to a computer, the computer needs to be running. This can be a hassle when you want to print from another devise such as a laptop in another room, or from a smart phone. One solution to solve this is to connect the printer by USB cable to the modem router. This allows prints to be made from the laptop or phone without the PC being turned on.
Most modern printers now have a WiFi function. A better solution than the one above, is to link the printer to the modem router by Wi-Fi. Connecting the printer to Wi-Fi can be fiddly to set up, as many printers only have a small LCD screen where you need to enter the Wi-Fi’s SSID and password.
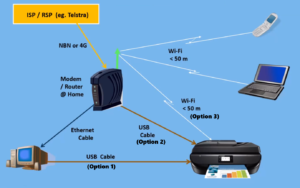
Figure 9 – Dave’s graphic depicting Printer Connection options
Printer connection Summary & Issues
Printers Connected via USB to a computer
- The PC has to be running for Phones or Laptop to be able to print
- The PC needs driver software for each particular printer
Printers Connected via a Router
- The router may have a USB port, but it may not have USB Printer connectivity. Routers such as Netgear’s smaller Night Hawk router, as used at Dave’s retirement village, only allow a USB stick containing photos etc.
Printers Connected via Wi-Fi
- Is the Wi-Fi signal stable at the distance needed?
- The user needs to enter Wi-Fi data into the printer, from the printer’s small LCD screen.
Printer – extra functions
Connected via Wi-Fi
- Wi-Fi connectivity is often overlooked or considered too hard
- The user needs to enter Wi-Fi data into printer which can be difficult
Scanning Documents
- Documents can be scanned by running apps already on a Windows computer e.g. Windows Fax & Scan.
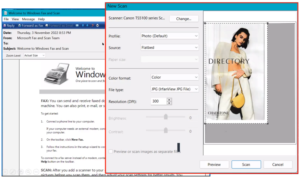
Figure 10 – Windows Fax & Scan, Scanning window
- OCR (Optical Character Recognition) is a function that converts a scanned document to text. There is no native OCR program in windows, but often these programs are bundled in with the printer. Dave uses a free OCR app from the Windows Store called “a9t9”. This program is easy to use and an excellent free alternative for Dave’s moderate needs, than retail OCR software.
Dave then demonstrated “Windows Fax & Scan” & the free OCR program “a9t9”as shown in Figure 11. OCR programs are unlikely to be 100% accurate. The accuracy will depend on the quality of the document being scanned and size of the original text. Dave suggests running a spell checker over the document to find obvious errors and then compare that with the original document. In “a9t9” the document can then be saved as text, a Word file or a pdf.
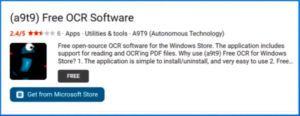
Figure 11 – a9t9 OCR Software application
Summary
Printers are a great accessory, but many users are not using all the functions available to them. i.e.
- Photocopier function
- Wi-Fi connectivity when it is available on a printer
- Photo printing from mobile phones is often overlooked.
Printer Issues & Difficulties
- Cost of replacement inks is greater than the printer itself. You then need to decide whether to buy genuine or 3rd party cartridges. Refilling cartridges is less of an option these days.
- Wi-Fi and OCR functions are often overlooked





Recent Comments